Feature Spotlight: Introducing multi-factor authentication in TYPO3 11.1

Secure handling of login credentials has never been more important than it is today. Cybercrime has become increasingly focused on companies—not just private individuals. A company website’s content management system can become a target, too, especially since most CMS installations are now connected to an organization’s internal PIM or ERM system. As a result, TYPO3 is constantly improving its tools to secure user accounts. TYPO3 uses, among others, award-winning hash algorithms, a notification system to inform administrators about unusual behavior, and provides several security configuration options, like enforcing secure HTTPS protocol for authentication.
These mechanisms can’t, however, protect you from the risks arising from weak or reused passwords. To address this concern, the IT world adopted multi-factor authentication (or MFA, for short) as a security standard. This method is currently considered the safest solution to increase user account protection. In multi-factor authentication, a user typically has to provide something he owns (this is where the “multi” factor comes in), in addition to the typical primary factor, something he knows, e.g. the username and password combination.
You may be asking: How can a user provide something he owns?
The simplest way is by entering a one-time password generated by a specific device or an application. Such code can only be used once and is only valid for a short time frame. To prove possession, users may also supply a real device, a so-called hardware token, which is quite similar to a USB-stick. Also providing an inherent factor, usually biometric data such as a fingerprint, is possible. The general rule of thumb is that anything that cannot be easily accessed by a third party could be considered something you own and therefore can be used as an additional factor.
Do you have further questions about multi-factor authentication?
TYPO3 and MFA
Since TYPO3 takes the security of its users really seriously, the recently released version 11.1 fully supports multi-factor authentication by default for every backend user. This is achieved through a completely new API allowing each TYPO3 installation to support as many MFA providers as needed. An MFA provider is one option that allows users to prove they possess an additional factor.
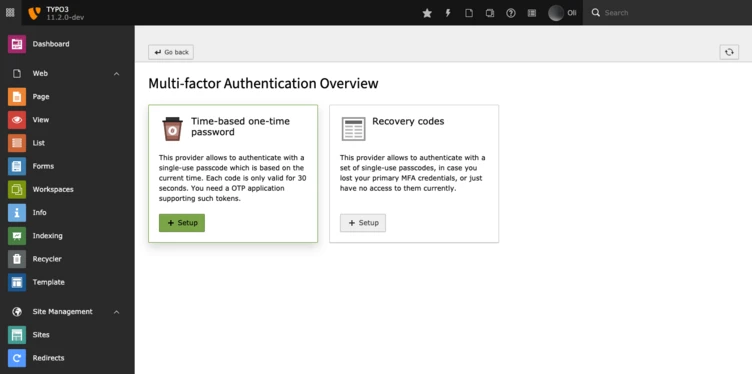
TYPO3 comes with two of these providers by default: The already mentioned time-based one-time password provider and the recovery codes provider. The recovery codes provider generates a set of codes the user must then store in a safe place. In the case he can not prove possession, e.g. because he lost his device that generates one-time passwords, these codes can be used as a fallback.
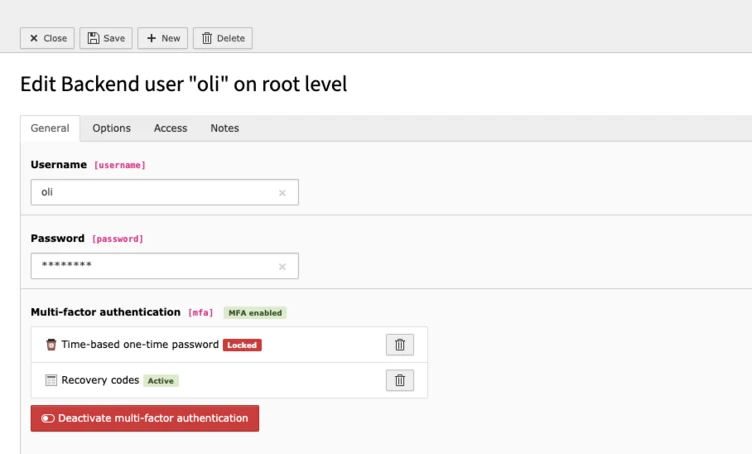
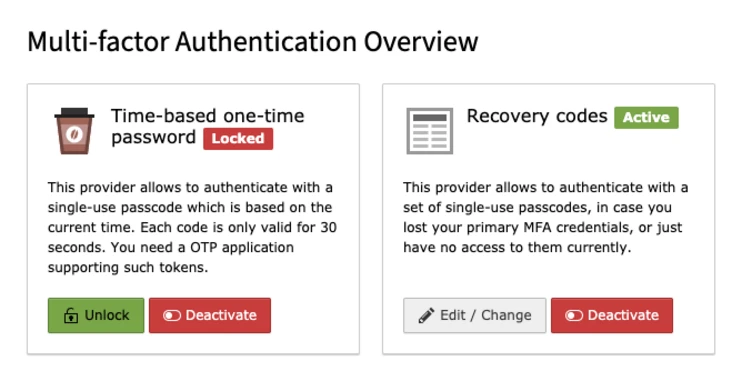
It’s important to mention that the recovery codes, as well as any other provider-generated codes, can only be used after the first factor (something you know, like a username and password) has been successfully verified. You can’t try out different codes without fulfilling the first step. Furthermore, TYPO3 will automatically lock a provider if it was unsuccessful three times in a row. Therefore, it’s simply not possible to circumvent the second step just by guessing.
How to set it up
To set up the time-based one-time password provider, you need an OTP-compatible device or application. Some examples are Google Authenticator, Authy, or 1Password.
If you have installed one of those applications or have your device at hand, navigate to your user settings. You will find a tab called “Account security”. This tab includes (next to the password change functionality) the “Multi-factor authentication providers” entry. The included button will get you to the new MFA configuration module, which displays all available MFA providers. To enter the setup view click on the Setup button.
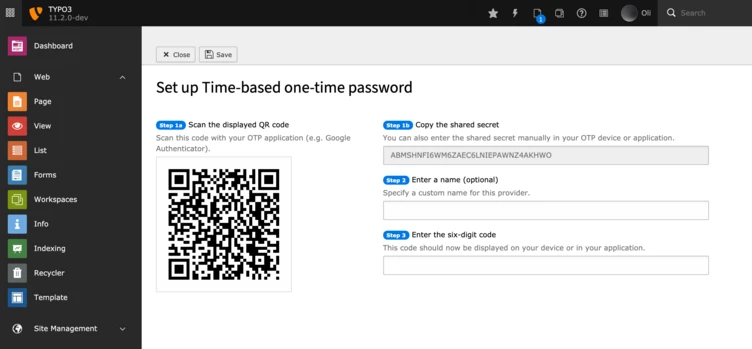
Setup Steps:
- Scan the displayed QR-code with your OTP application
- Alternatively enter the displayed shared secret into your OTP application or device
- Optionally define a custom name for this provider
- Enter the six-digit code generated by your OTP application or device
- Activate the provider by submitting the form (click on the save button)
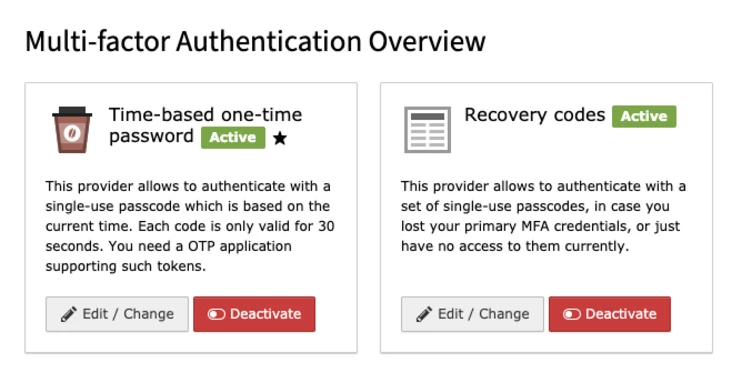
Congratulations, you have successfully activated your first MFA provider and thereby increased your account security tremendously. To make use of MFA’s full potential we also recommend activating the recovery codes provider. To do so, enter the setup view of the recovery codes provider, copy the displayed recovery codes in a safe place and submit the form. The activation will take some time since TYPO3 will encrypt your codes and store them securely.
How to authenticate
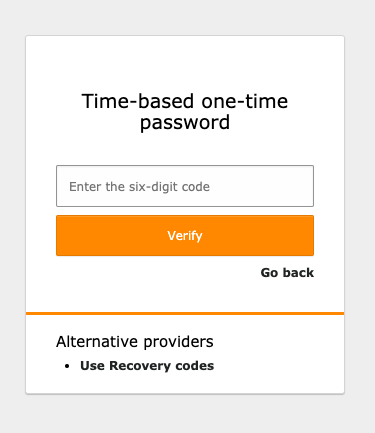
From now on, whenever you log into the TYPO3 backend, you’ll have to provide the additional factor after successfully passing the first one, e.g. your username and password. In the case of the one-time password provider, you have to enter the generated six-digit code from your OTP application or device and verify afterwards. If the one-time password can be verified, you will automatically be forwarded to the backend.
In case you activated more than one provider, e.g. one-time password and recovery codes, you can freely select which MFA provider should be used for the additional authentication step on every authentication attempt. This comes in handy if you use different devices depending on your location or are temporarily unable to use your main provider, e.g., because you lost the corresponding device or just don’t have immediate access to it. To switch to an alternative provider, just click on the corresponding link below the current provider’s authentication mask.

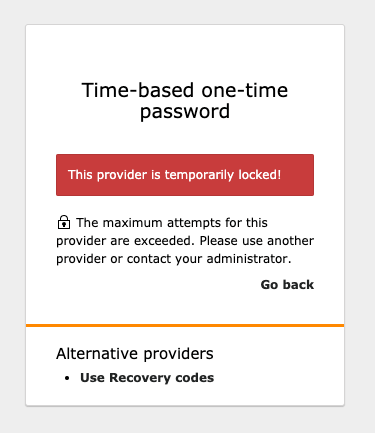
You’ll be notified if one of your providers gets locked by TYPO3. In that case, you won’t be able to use the locked provider anymore. If you nevertheless manage to log into the backend with another active provider, you may want to unlock the previously locked provider in the MFA configuration module.
If you’ve lost your device irretrievably, just unlocking the provider won't help and you have to completely deactivate the MFA provider. Afterwards, you can start over. Of course, this action can be performed at any time, in case you just don't need a provider any longer or want to switch devices.

Administration of users’ MFA
As an administrator, you may ask: How can I manage my users’ MFA providers? Am I somehow able to enforce that users set up MFA at all?
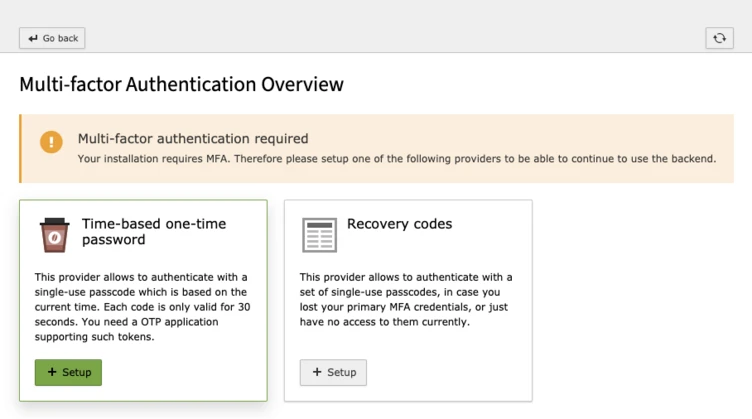
Good news. TYPO3 has also implemented various configuration and administration options. Your administered installation only fully benefits from MFA when every user has activated at least one provider. This can easily be enforced by setting the $GLOBALS['TYPO3_CONF_VARS']['BE']['requireMfa'] variable.
It’s likely that not every provider is suitable for your users. This is why you are equipped with the ability to define the providers available for a user or user group straightforwardly in the corresponding records.
You may also want to recommend a specific provider for your users. This is possible, using the $GLOBALS['TYPO3_CONF_VARS']['BE']['recommendedProvider'] variable. Since this defines a provider globally for all users, you’ll also want to have a look at the related user TSconfig option “auth.mfa.recommendedProvider” which enables you to recommend a specific provider on a per user basis.
Last but not least, there will probably be the moment when you receive an email from one of your users, notifying you that he has locked himself out. No worries, you can rest easy since TYPO3 allows you to deactivate MFA for every user in the corresponding user record. This allows the user to log in and set up MFA again. By the way, the “backend user module” gives you an overview of your users’ current MFA status—whether MFA is enabled or currently locked—at any time.
Enable multi-factor authentication today
Whether you’re an administrator or an editor, your account could be at risk on any given day. TYPO3 addresses these risks with a state-of-the-art security mechanism, and we’re already evaluating the next steps to improve your account’s security even more. So don’t hold back, activate your first MFA provider today—trust us, it’s easy.